2018 New CompTIA SY0-501 Exam Dumps with PDF and VCE Free Updated Today! Following are some new SY0-501 Exam Questions:
https://www.braindump2go.com/sy0-501.html
2.2018 New SY0-501 Exam Questions & Answers:
https://drive.google.com/drive/folders/1QYBwvoau8PlTQ3bugQuy0pES-zrLrRB1?usp=sharing
QUESTION 23
A database backup schedule consists of weekly full backups performed on Saturday at 12:00 A.m. and daily differential backups also performed at 12:00 A.m. If the database is restored on Tuesday afternoon, which of the following is the number of individual backups that would need to be applied to complete the database recovery?
A. 1
B. 2
C. 3
D. 4
Answer: B
QUESTION 24
Which of the following technologies employ the use of SAML? (Select TWO).
A. Single sign-on
B. Federation
C. LDAP
D. Secure token
E. RADIUS
Answer: AB
QUESTION 25
An organization is using a tool to perform a source code review. Which of the following describes the case in which the tool incorrectly identifies the vulnerability?
A. False negative
B. True negative
C. False positive
D. True positive
Answer: C
QUESTION 26
In a corporation where compute utilization spikes several times a year, the Chief Information Officer (CIO) has requested a cost-effective architecture to handle the variable capacity demand. Which of the following characteristics BEST describes what the CIO has requested?
A. Elasticity
B. Scalability
C. High availability
D. Redundancy
Answer: A
QUESTION 27
A Security analyst is diagnosing an incident in which a system was compromised from an external IP address. The socket identified on the firewall was traced to 207.46.130.6666. Which of the following should the security analyst do to determine if the compromised system still has an active connection?
A. tracert
B. netstat
C. Ping
D. nslookup
Answer: B
QUESTION 28
Which of the following BEST describes an important security advantage yielded by implementing vendor diversity?
A. Sustainability
B. Homogeneity
C. Resiliency
D. Configurability
Answer: C
QUESTION 29
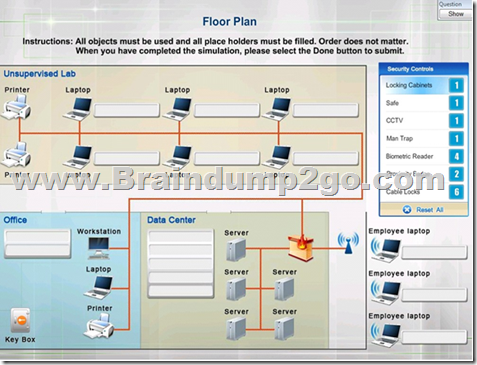
Drag and Drop Question
You have been tasked with designing a security plan for your company.
Drag and drop the appropriate security controls on the floor plan.
Instructions:
All objects must be used and all place holders must be filled Order does not matter
When you have completed the simulation, please select the Done button to submit.
Answer:
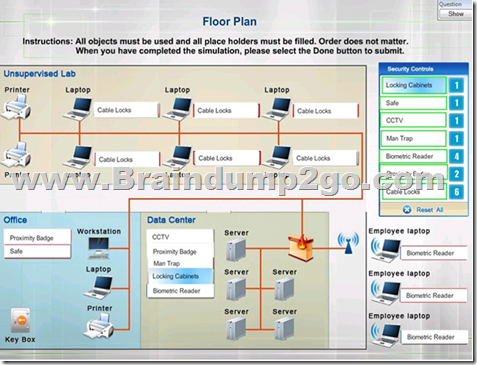
Explanation:
Cable locks – Adding a cable lock between a laptop and a desk prevents someone from picking it up and walking away
Proximity badge + reader
Safe is a hardware/physical security measure
Mantrap can be used to control access to sensitive areas.
CCTV can be used as video surveillance.
Biometric reader can be used to control and prevent unauthorized access. Locking cabinets can be used to protect backup media, documentation and other physical artefacts.
QUESTION 30
Which of the following encryption methods does PKI typically use to securely protect keys?
A. Elliptic curve
B. Digital signatures
C. Asymmetric
D. Obfuscation
Answer: B
QUESTION 31
Which of the following characteristics differentiate a rainbow table attack from a brute force attack? (Select TWO).
A. Rainbow table attacks greatly reduce compute cycles at attack time.
B. Rainbow tables must include precompiled hashes.
C. Rainbow table attacks do not require access to hashed passwords.
D. Rainbow table attacks must be performed on the network.
E. Rainbow table attacks bypass maximum failed login restrictions.
Answer: BE
QUESTION 32
Which of the following BEST describes a routine in which semicolons, dashes, quotes, and commas are removed from a string?
A. Error handling to protect against program exploitation
B. Exception handling to protect against XSRF attacks
C. Input validation to protect against SQL injection
D. Padding to protect against string buffer overflows
Answer: C
QUESTION 33
Which of the following is an important step to take BEFORE moving any installation packages from a test environment to production?
A. Roll back changes in the test environment
B. Verify the hashes of files
C. Archive and compress the files
D. Update the secure baseline
Answer: A
!!!RECOMMEND!!!
1.2018 New SY0-501 Exam Dumps (PDF and VCE)Share:
https://www.braindump2go.com/sy0-501.html
2.2018 New SY0-501 Study Guide Video: